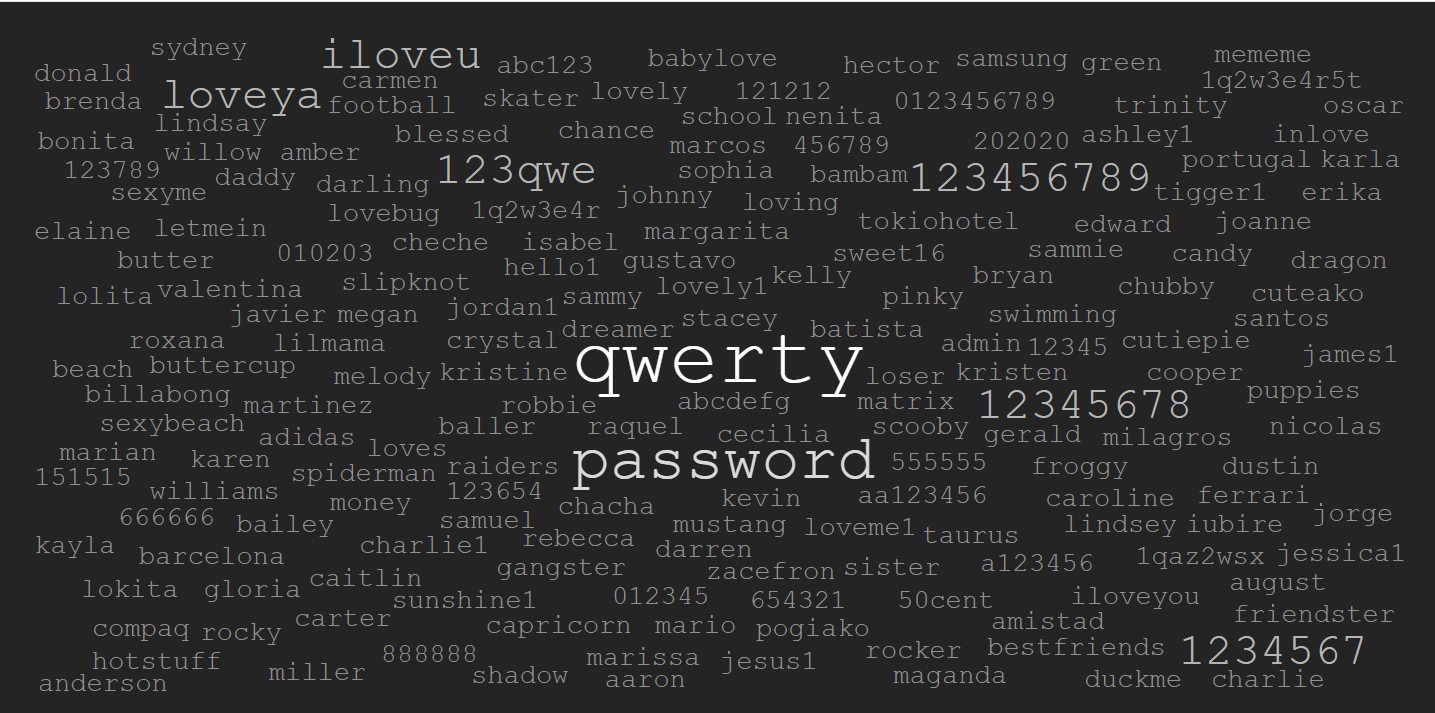
Passwords have been the most widely used authentication mechanism in the technological world, due to their simplicity. Although security researchers and engineerings struggle to replace them with other authentication methods such as biometric authentication, token authentication, certificate authentication or enhance them via multi-factor authentication (a combination of the pre-mentioned), they are still widely used. Although passwords are not inherently unsafe, they are difficult to handle by humans. Keeping a password safe and private, while at the same time remembering the password, choosing a strong and as random as possible password e.t.c are only some of the challenges people have to face. As a result, many users choose predictable and easy to guess passwords. So easy, that they are already contained in lists of words (aka dictionaries) or can be generated by re-spelling those words (e.g password –> p@$$w0rd).
In cryptanalysis and computer security, a dictionary attack is a form of brute force attack technique i for defeating a cipher or authentication mechanism, by trying to determine its decryption key or passphrase by trying thousands or millions of likely possibilities, often from lists obtained from past security breaches. In contrast, a heuristic attack that makes good use of information, in order to reduce the time-complexity, brute-force attacks can be time consuming and uneffective for strong passwords. On the other side of the coin, brute-force attack is a great way to exploit authentication schemes that do not use strong password policies
Tools & Resources
Common open-source tools used for this purpose are Burp Suite and hydra for online login form attacks, fcrackzip for cracking zip protected archives, L0phtCrack—a tool for cracking Windows passwords, hashcat a tool for matching passwords with unsalted hashes, Aircrack-ng a tool for attacking wireless password protected network and more.

Wordlists of common usernames, social media passwords, ssh passwords etc (such as rockyou.txt , ssh_passwd.txt, usernames.txt) exist publicly on the internet and are used by malicious and ethical hackers in order to brake low security authentications.</a attack has been identified on a communications provider which, as a result, has for a short time prevented access to a number of sites, including

Building a strong cybersecurity ecosystem at the heart of discussions at the Informal Meeting of European Telecommunications Ministers
The Informal Meeting of Ministers of Telecommunications took place on March 8 and 9, 2022, under the French Presidency, in the cities of Paris and Nevers, France. Cyprus was represented by the Deputy Minister of