The term engineering can be defined as:
The action of working artfully to bring something about.
Oxford Dictionary Tweet
In other words, the job of an engineer is to apply his theoretical knowledge and make use of his skills in order to develop a system – i.e “a set of things working together as parts of a mechanism or an interconnecting network; a complex whole.” The inverse function of engineering is reverse engineering. Given the system as a whole, what information can one extract about the internal components and functions of the system? The answer to this question is given by reverse engineering.
In the context of cyber-security, software reverse engineering (SRE) is narrowed down to deconstructing programs. A program is a system, and its made of raw code – just like a bridge is made of steel, concrete etc. And just like a bridge, this raw code (officially known as the source code) is not what the end user experiences. The end user experences the bridge as a whole, as a compilation of its materials. Respectively, in computer science, the end user experiences the program as a whole, as a compiled code made of zeros and ones. The programmer writes the source code, the reverse engineer reads the assembly code. With that being said, reverse engineering can be seen as the process of extracting information about the source code, from the final executable.
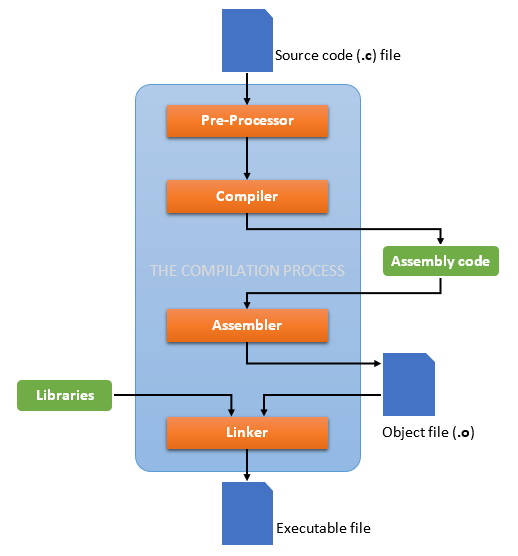
Reverse engineering serves multiple purposes. Legitimate ones and malicious one. SRE can be used to analyze a malware to determine the potential impact, the origin and the functionality of a malware (e.g virus, trojan horse, worm etc). But SRE can be also used as an exploitation tool by malicious users, in order to discover sensitive information that may be contained in the program such as passwords, API key details etc. Hence, the skill of reverse engineering is an important asset for a security professional.
It requires a solid understanding of assembly language, and the state-of-art SRE tools. Some of those tools are:
- Ghidra: An open-source SRE tool developed by NSA
- Radare2: A complete framework for reverse-engineering and analyzing binaries; composed of a set of small utilities that can be used together or independently from the command line
- x64dbg: A tool for reverse engineering windows fils.
- Sandboxie: A sandbox to safely run programs in order to study their behavior
- Wireshark: A tool user mainly for packet sniffing. But nevertheless, an important RE tool for network protocols.
P.S: Have you tried to break in through the layers of Gandalf’s defense by reverse engineering the executable? There may be hiding an interesting string…
Train/test your SRE skills with this challenge:
ECSC CHALLENGE

You shall not pass!
. Can you break in, through the layers of Gandalf’s defense and reveal the secret flag?






