Researchers Uncover 'Process Ghosting' — A New Malware Evasion Technique
Cybersecurity researchers have disclosed a new executable image tampering attack dubbed “Process Ghosting” that could be potentially abused by an attacker to circumvent protections and stealthily run malicious code on a Windows system.
“With this technique, an attacker can write a piece of malware to disk in such a way that it’s difficult to scan or delete it — and where it then executes the deleted malware as though it were a regular file on disk,” Elastic Security researcher Gabriel Landau said. “This technique does not involve code injection, Process Hollowing, or Transactional NTFS (TxF).”
Process Ghosting expands on previously documented endpoint bypass methods such as Process Doppelgänging and Process Herpaderping, thereby enabling the veiled execution of malicious code that may evade anti-malware defenses and detection.
Process Doppelgänging, analogous to Process Hollowing, involves injecting arbitrary code in the address space of a legitimate application’s live process that can then be executed from the trusted service. Process Herpaderping, first detailed last October, describes a method to obscure the behavior of a running process by modifying the executable on disk after the image has been mapped in memory.
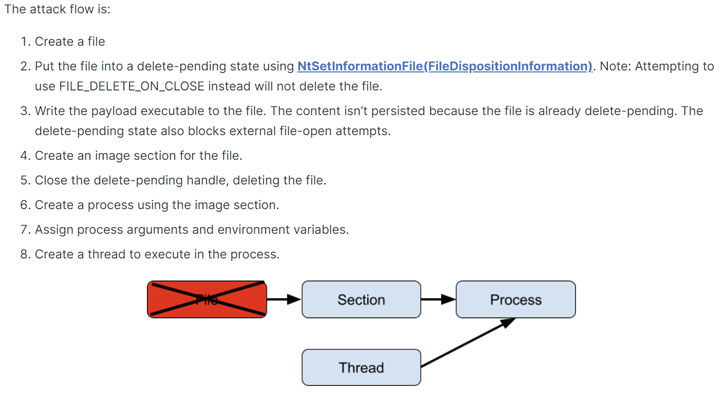
In a proof-of-concept (PoC) demo, the researchers detailed a scenario wherein Windows Defender attempts to open a malicious payload executable to scan it, but fails to do so because the file is in a delete-pending state, and then fails again as the file is already deleted, thus allowing it to be executed unimpeded.
Microsoft, for its part, has since released an updated version of its Sysinternals Suite earlier this January with an improved System Monitor (aka Sysmon) utility to help detect Process Herpaderping and Process Hollowing attacks.






