New Leak Reveals Abuse of Pegasus Spyware to Target Journalists Globally
A sweeping probe into a data leak of more than 50,000 phone numbers has revealed an extensive misuse of Israeli company NSO Group’s Pegasus “military-grade spyware” to facilitate human rights violations by surveilling heads of state, activists, journalists, and lawyers around the world.
Dubbed the “Pegasus Project,” the investigation is a collaboration by more than 80 journalists from a consortium of 17 media organizations in 10 countries coordinated by Forbidden Stories, a Paris-based media non-profit, along with the technical support of Amnesty International.
“The Pegasus Project lays bare how NSO’s spyware is a weapon of choice for repressive governments seeking to silence journalists, attack activists and crush dissent, placing countless lives in peril,” Amnesty International’s Secretary-General, Agnès Callamard, said.
“These revelations blow apart any claims by NSO that such attacks are rare and down to rogue use of their technology. While the company claims its spyware is only used for legitimate criminal and terror investigations, it’s clear its technology facilitates systemic abuse. They paint a picture of legitimacy, while profiting from widespread human rights violations,” Callamard added.
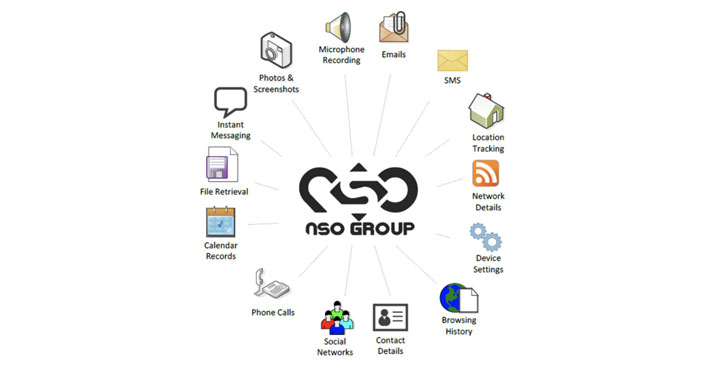
NSO Group is the maker of a cyber-surveillance weapon called “Pegasus,” which, when surreptitiously installed on victims’ iPhone and Android devices, enables an attacker to harvest emails, SMS messages, media, calendars, calls, and contact information, as well as chat content from messaging apps like WhatsApp, Telegram and Signal, and stealthily activate the phone’s microphone and camera.
The investigation has so far identified 180 journalists and more than 600 politicians and government officials, spanning across more than 50 countries, even as the timeline of the attacks spread over a seven-year period from 2014 up to as recently as July 2021. However, Rwanda, Morocco, India, and Hungary denied having used Pegasus to hack the phones of the individuals named in the list.
Troublingly, a forensic analysis of 67 mobile devices showed the intrusions involved the ongoing use of so-called “zero-click” exploits — which do not require any interaction from the target — dating all the way back to May 2018. In one instance highlighted by Amnesty International, the compromise is believed to have leveraged multiple zero-days in iMessage to attack a fully patched iPhone 12 running iOS 14.6 in July 2021.
“All this indicates that NSO Group can break into the latest iPhones,” Citizen Lab’s Bill Marczak said in a series of tweets. “It also indicates that Apple has a MAJOR blinking red five-alarm-fire problem with iMessage security that their BlastDoor Framework (introduced in iOS 14 to make zero-click exploitation more difficult) ain’t solving.”






