The U.S. Department of Justice (DOJ) sentenced a Russian man for operating a large-scale digital advertising fraud scheme called ‘Methbot’ (‘3ve’) that stole at least $7 million from American companies.
Aleksandr Zhukov, aka the “King of Fraud,” was sentenced to 10 years of imprisonment in the U.S. and ordered to forfeit the total sum of his assets, amounting to $3,827,493.
That’s roughly one million USD less than what the scammer pocketed from the fraud, with the remaining 25% going to his co-conspirators.
Zhukov was arrested in Bulgaria in 2018 and extradited to the United States in the following year.
The man was convicted of wire fraud conspiracy, wire fraud, money laundering, and money laundering conspiracy in May 2021.
The U.S. District Court of the Eastern District of New York has just announced the sentence and will have to spend another seven years in prison.
A massive scheme
Zhukov and his co-conspirators set up a massive ad-fraud botnet named “Methbot,” also known as “3ve”, which consisted of at least 700,000 active infections managed by a thousand data center nodes, and which used 750,000 IP addresses.
These bots generated false traffic to sites between September 2014 and December 2016, thus creating fake impressions on advertisements.
Advertisers paid Zhukov large sums to drive their online marketing campaigns, and the fraudster did so on cloned, spoofed sites.
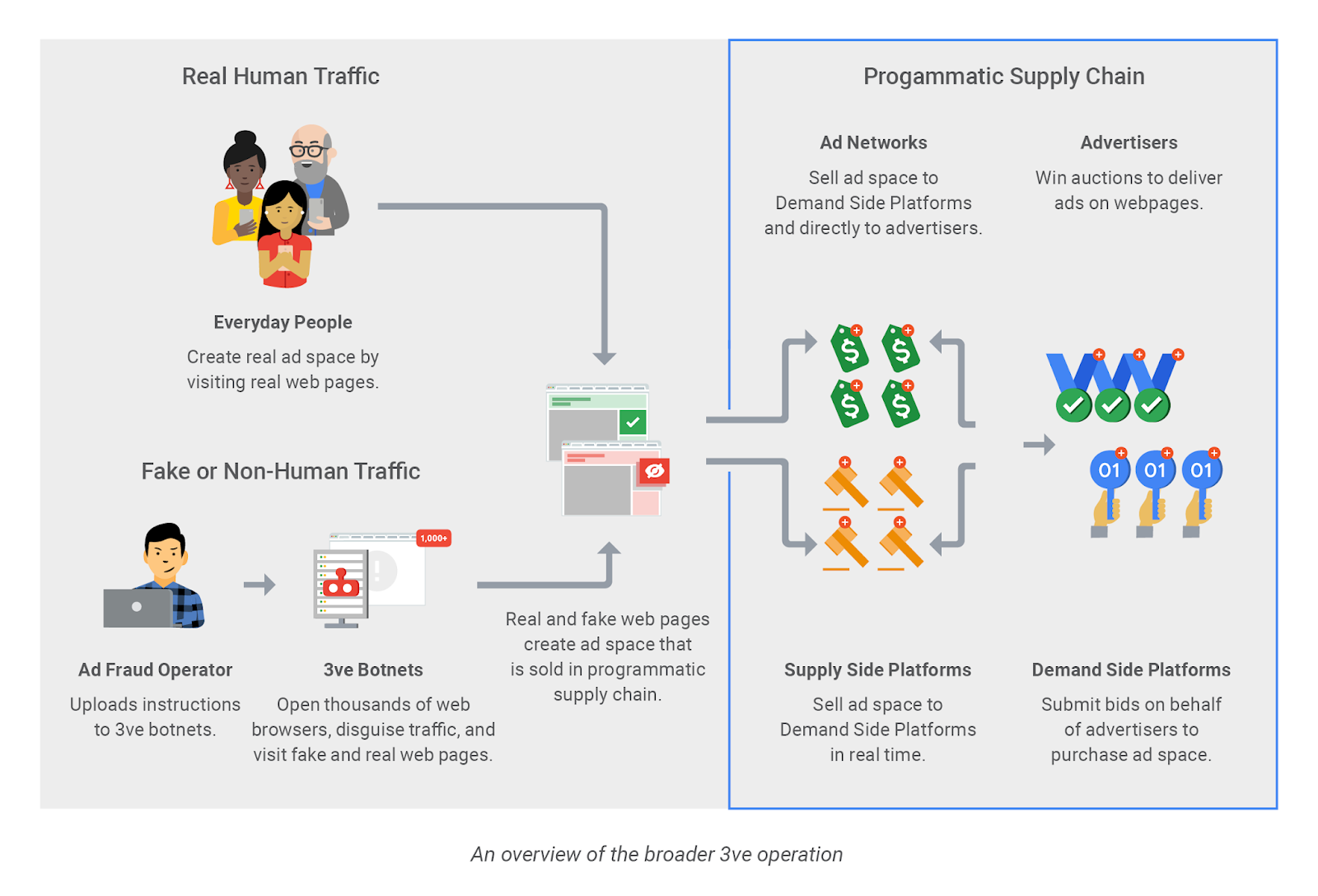
In total, it is believed that scammer spoofed at least 6,000 websites, including those of The New York Times and the New York Post.
“To create the illusion that human internet users were viewing the advertisements loaded onto these spoofed webpages, Zhukov and his co-conspirators programmed the bots to appear and behave like human internet users.” Reads the U.S. DoJ announcement
“Zhukov and his co-conspirators also programmed the bots to click around a screen a randomly determined number of times, simulate a mouse moving around and scrolling down a webpage, start and stop a video player midway, bypass captchas, accept cookies, and falsely appear to be signed into popular social media services such as Facebook, Twitter, and Google.”
None of the ads that companies paid Zhukov to run were ever displayed on real sites, and none of them were ever seen by human internet users.
Zhukov’s only expense for running this fraud operation was the 25% cut of his co-conspirators, the programmer salaries, and the renting costs of 2,000 servers located in the U.S.






